User Federation with Keycloak (OpenID)
V1.0 – October 2024
| Version | Author | Description |
|---|---|---|
| V1.0 – 2024-10-15 | Diogo Hatz d50037923 | Initial Version |
| V1.0 – 2024-10-15 | Wisley da Silva Paulo 00830850 | Document Review |
Objective
This document aims to present the procedures required to implement identity federation configuration in Huawei Cloud (Service Provider) through an identity provider (IdP), such as RedHat SSO or Keycloak. In this example, the protocol used for identity federation will be OpenID, mapping users from the identity provider to virtual users in Huawei Cloud.
In the diagram below, you can see the authentication process flow in Huawei Cloud using an IdP.
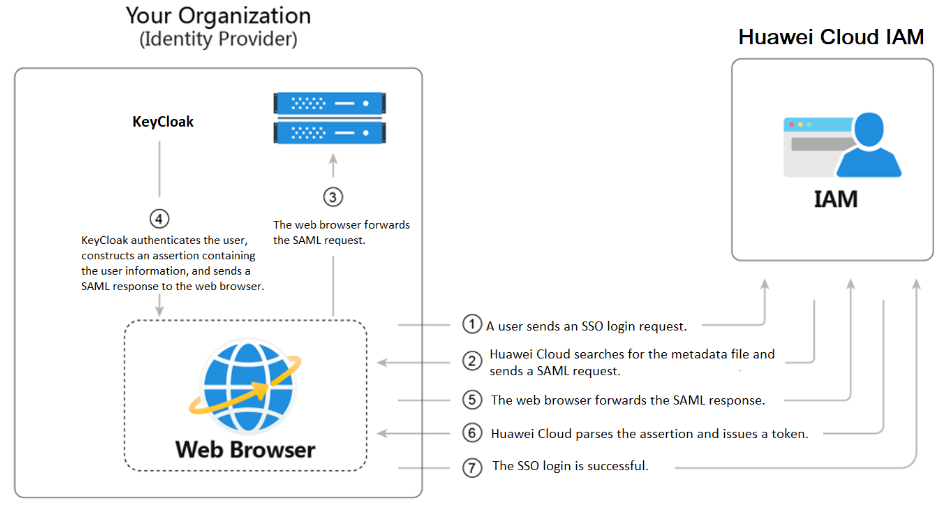
Keycloak
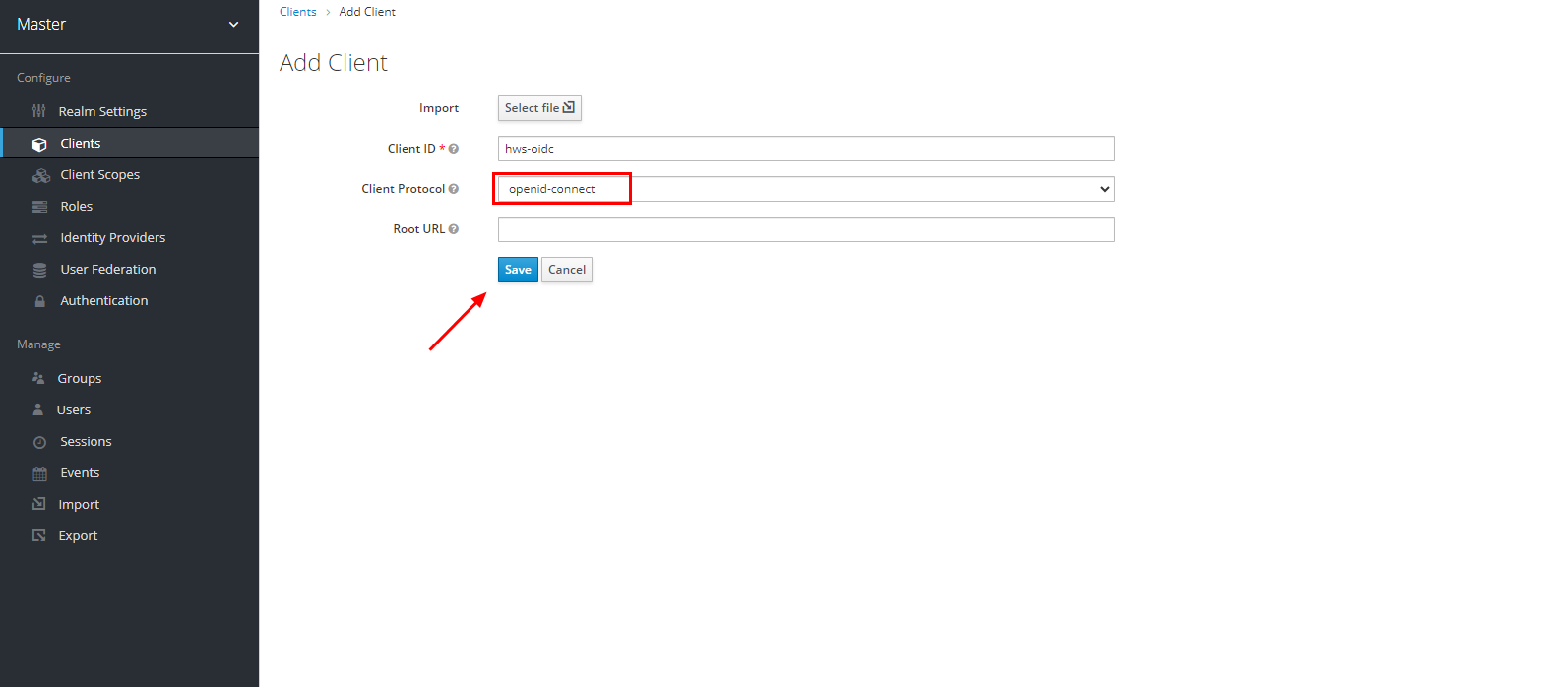
First, you need to configure the identity provider (IdP). To do this, access the IdP (Keycloak) configuration page and navigate to the “Clients” section. Click “Create” to create a new client.
Select “Client Protocol” as “openid-connect” and enter “hws-oidc” in the “Client ID” field. Once done, click “Save” to create the client.
Navigate to the Huawei Cloud client you created and click “Edit” to edit the client settings.
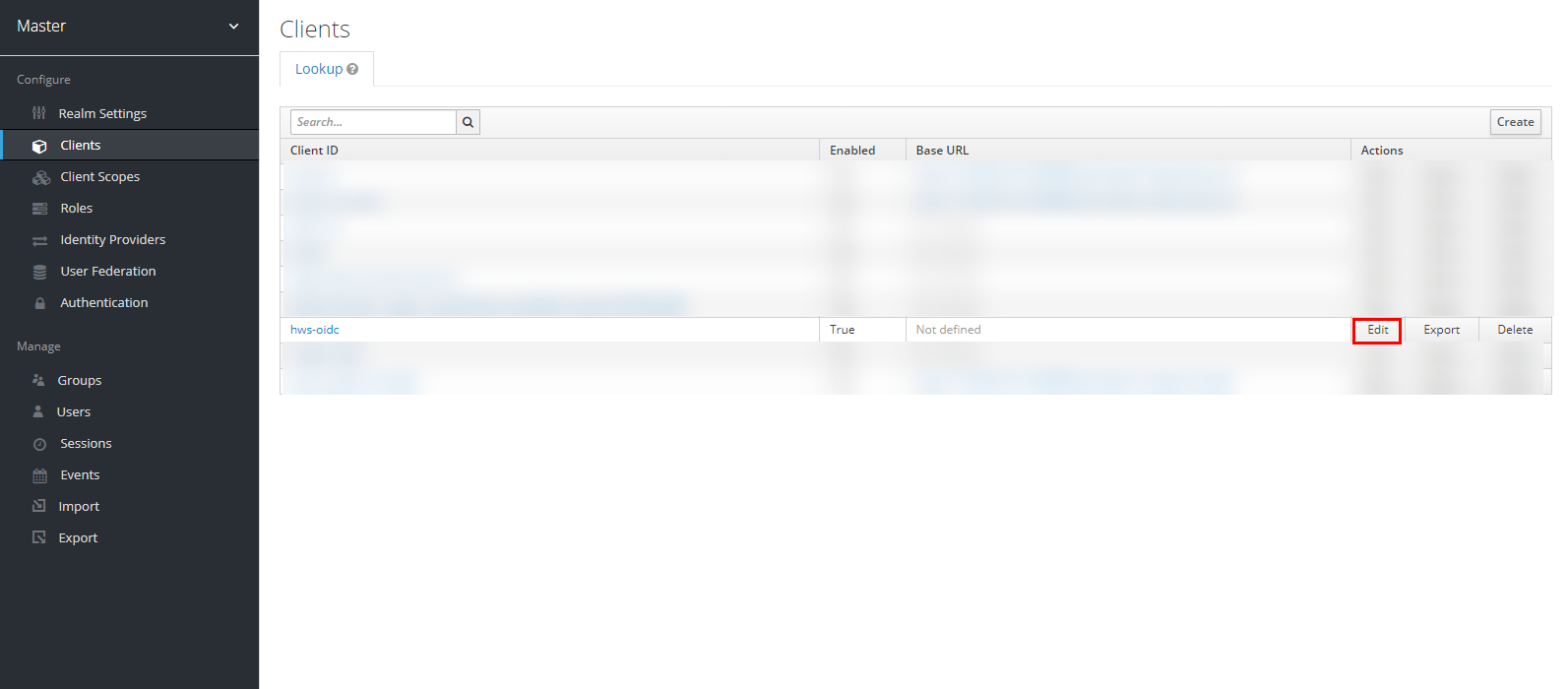
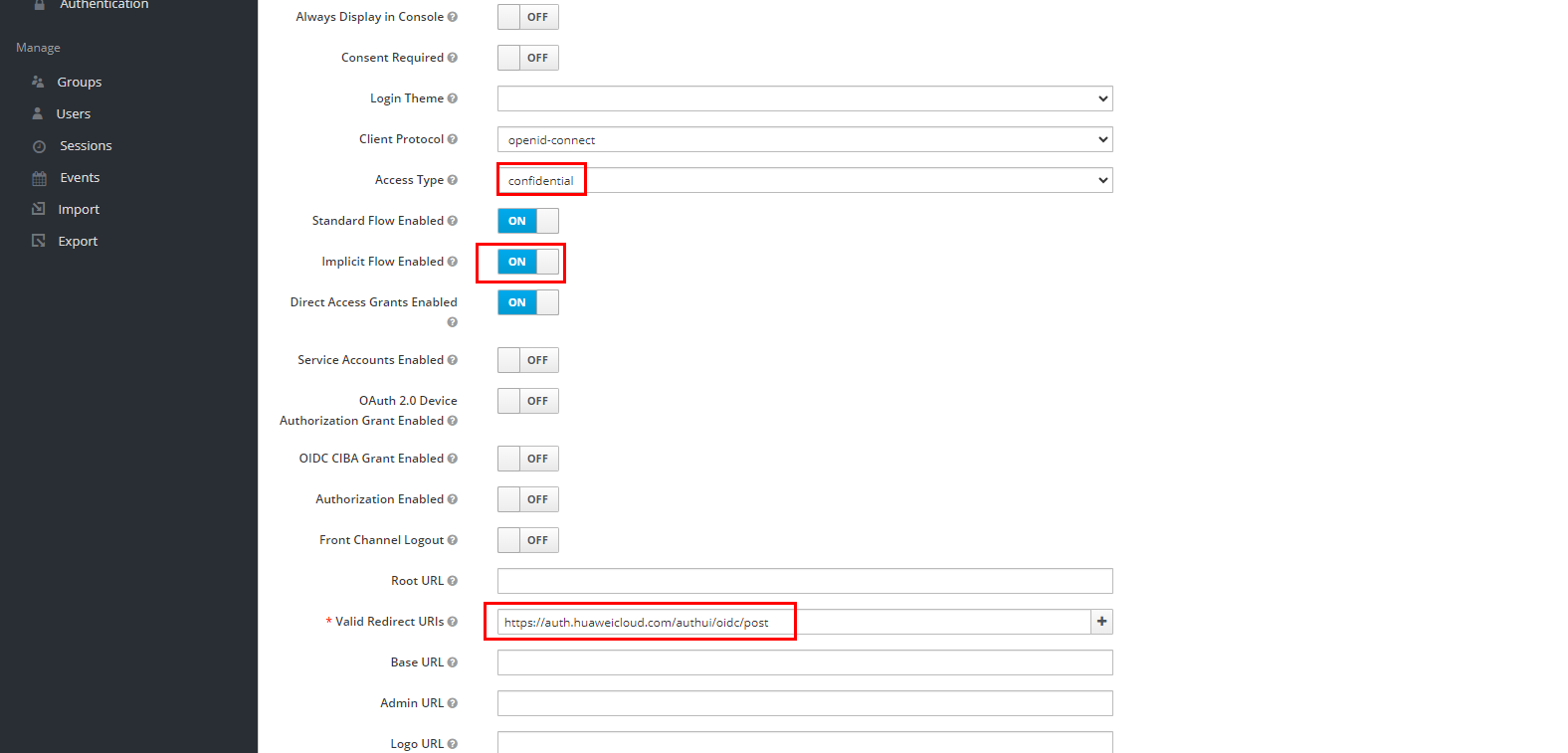
Enable the “Implicit Flow Enabled” option, change the “Access Type” field to “confidential” and insert the following hyperlink in the “Valid Redirect URIs” field: https://auth.huaweicloud.com/authui/oidc/post. Once done, click “Save” to save the changes made.
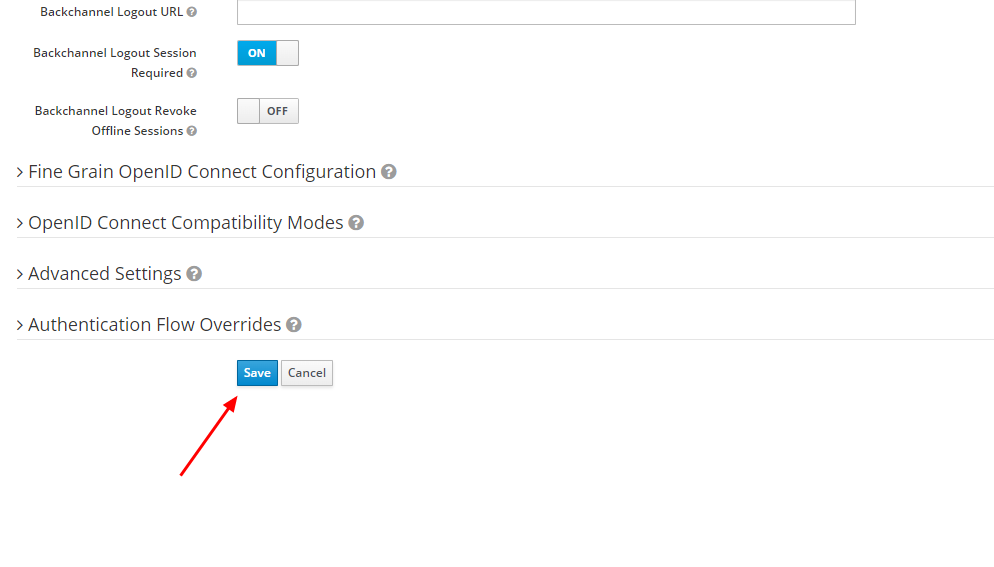
Navigate to the “Mappers” section, still in the Huawei Cloud client settings, and click “Create” to create a mapper for the username.
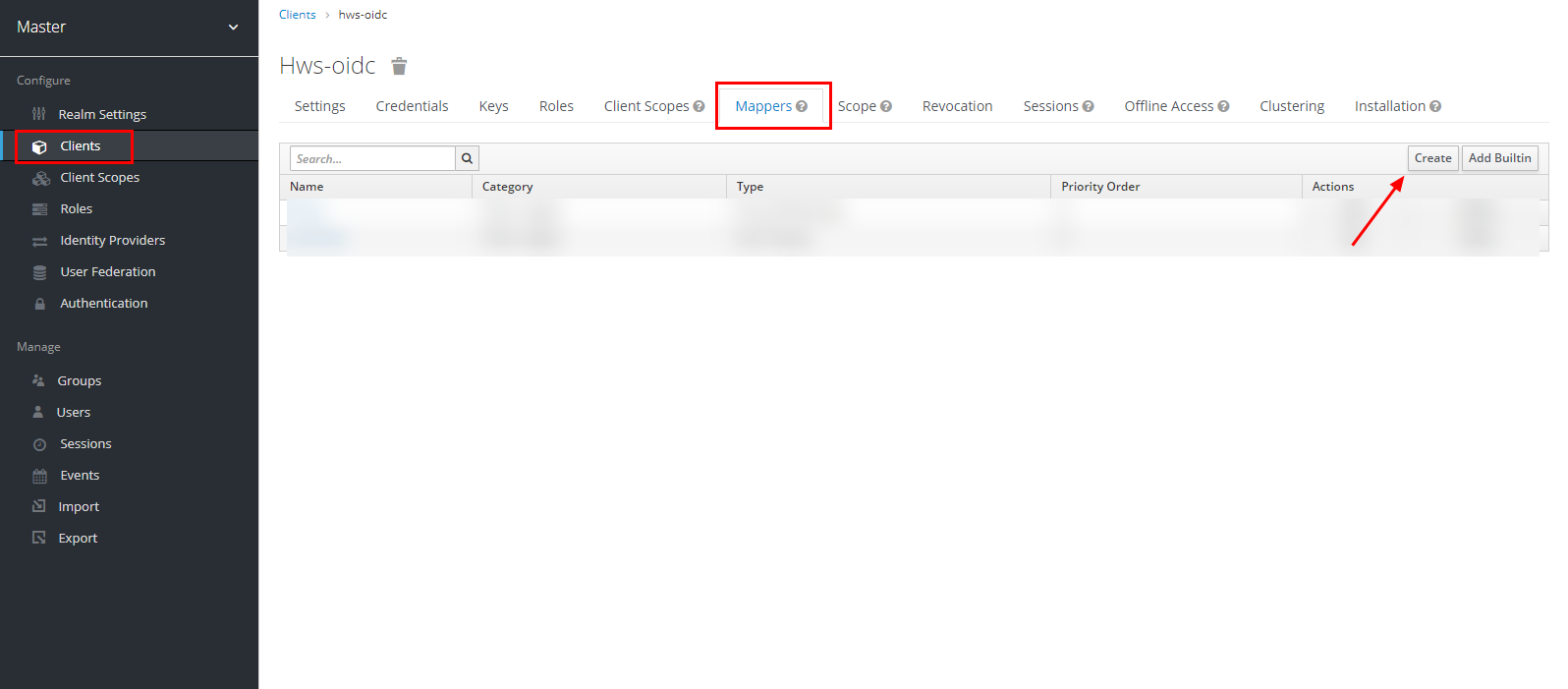
Select the “Mapper Type” as “User Property” and fill in the remaining fields as shown in the image below.
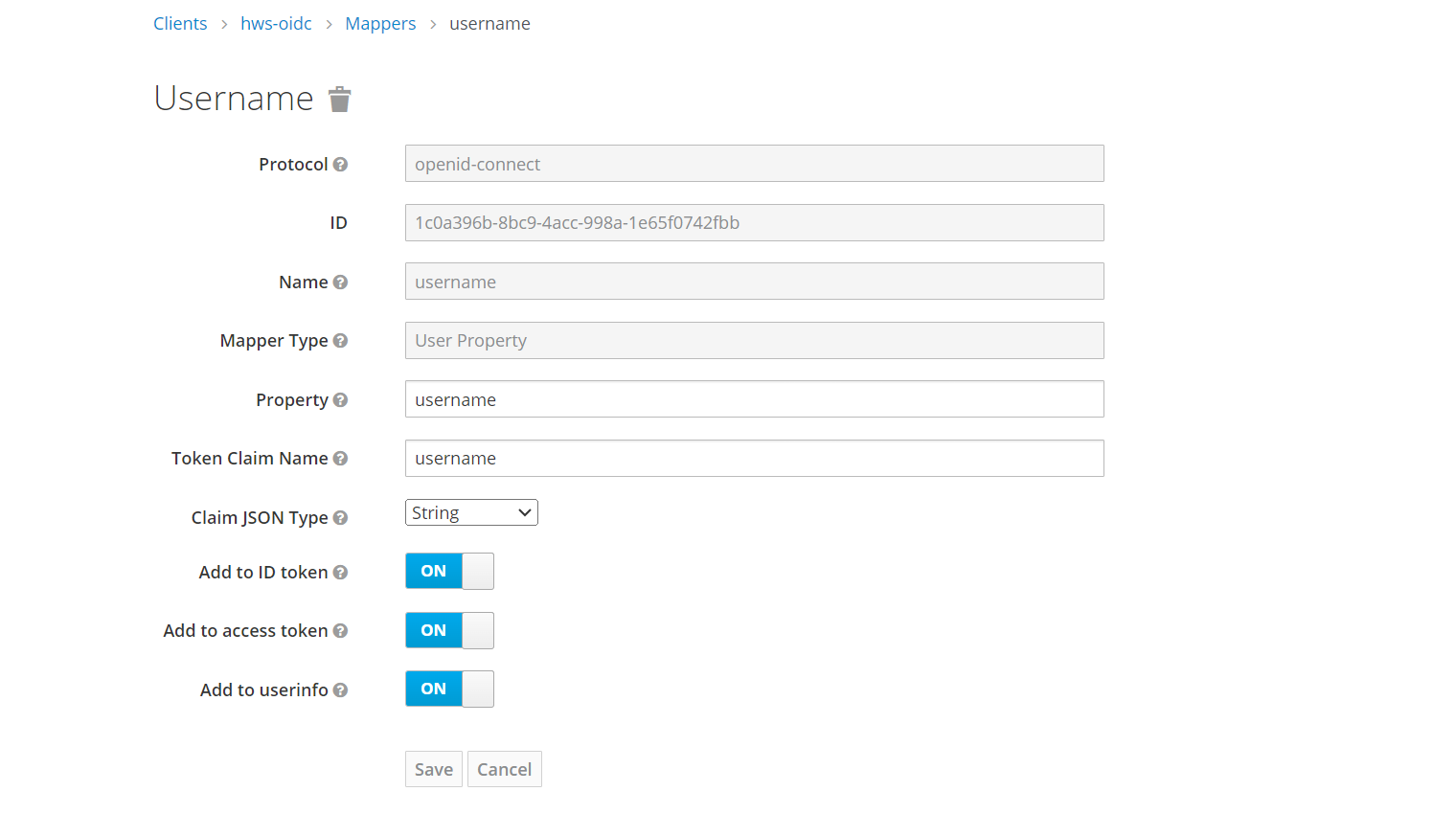
Navigate once again to the “Mappers” section, still in the Huawei Cloud client settings, and click “Create” to create a mapper for the group.

Select the “Mapper Type” as “Group Membership”, disable the “Full group path” option and fill in the remaining fields as shown in the image below.
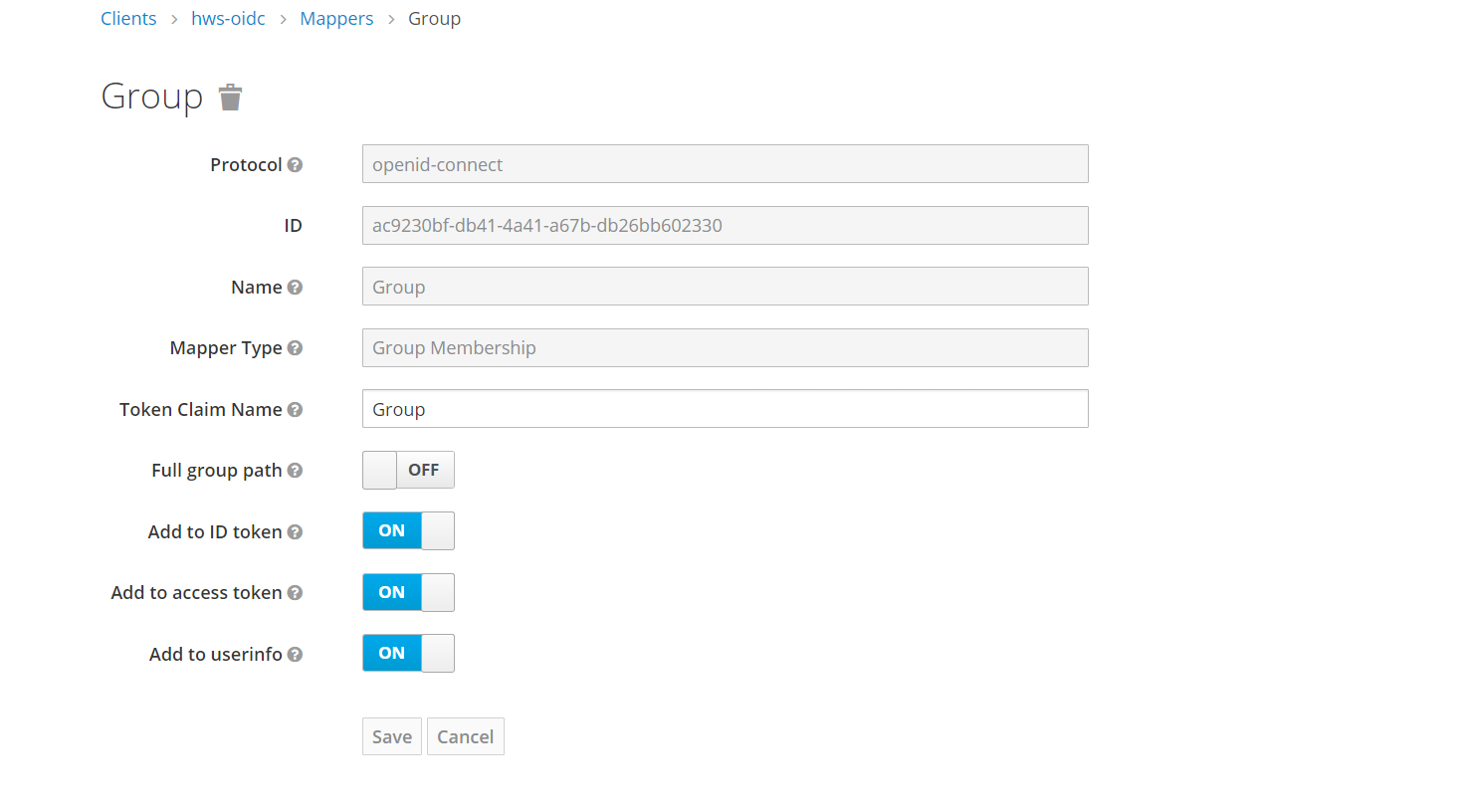
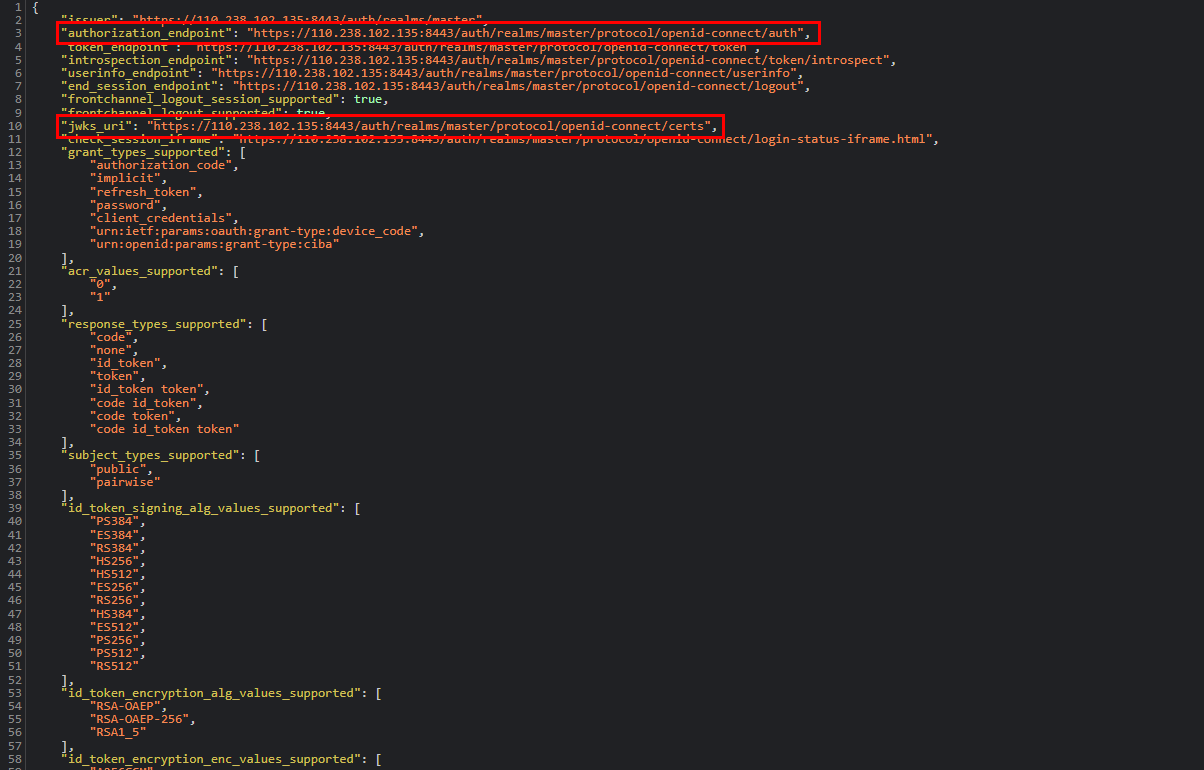
To perform Huawei Cloud user federation, users must first exist. If there is no user created in Keycloak, create a user. Navigate to the “Realm Settings” section and click on “OpenID Endpoint Configuration” in the “Endpoints” subsection.
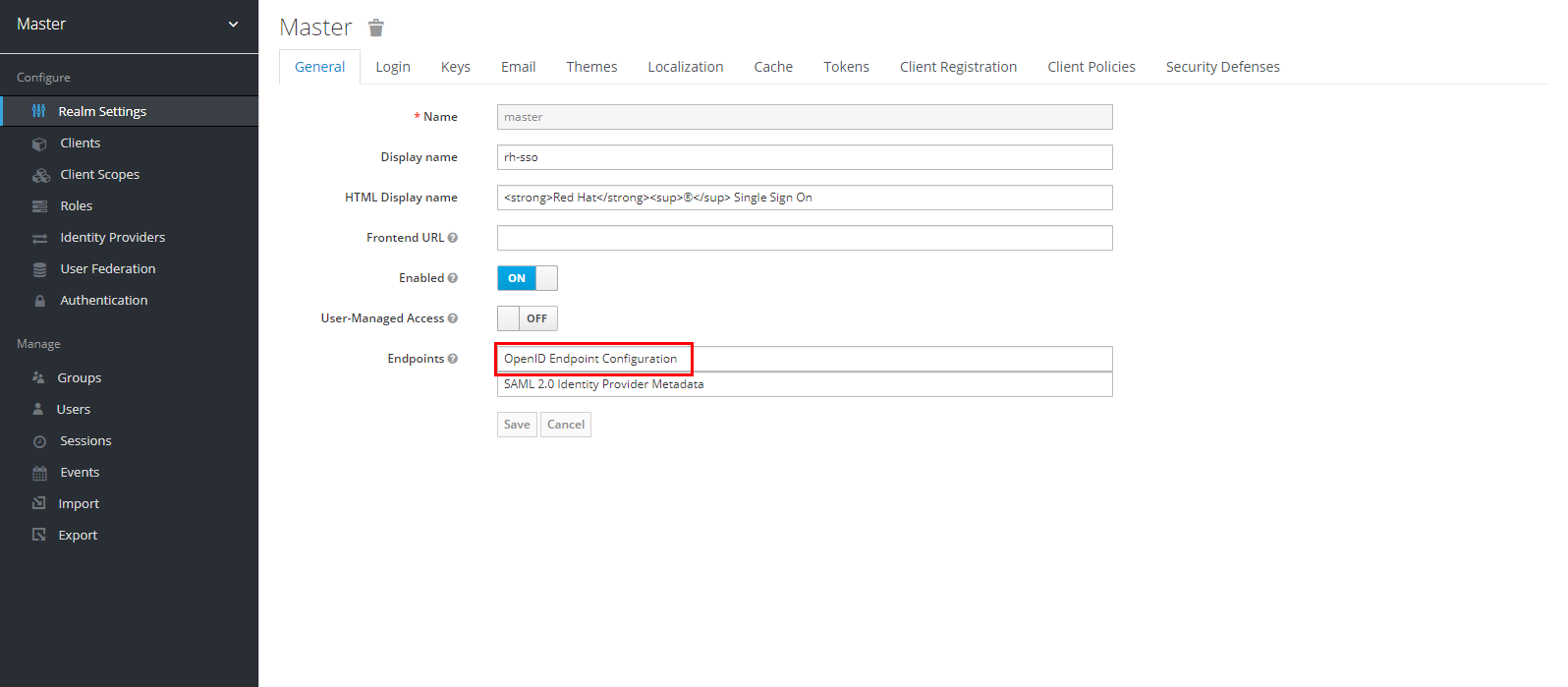
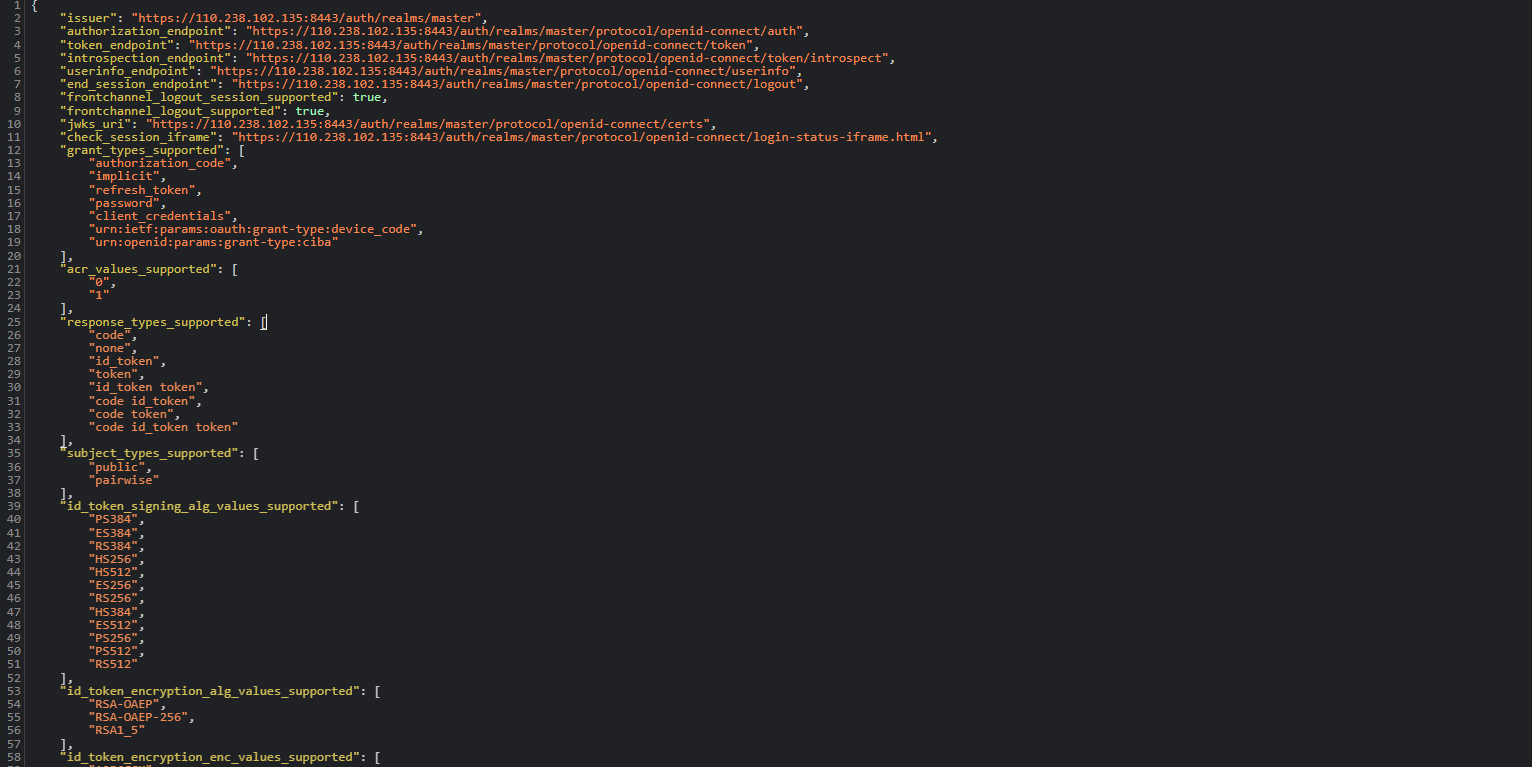
Note the following parameters, which will need to be configured on the service provider (Huawei Cloud) side: “authorization_endpoint” and “jwks_uri”.
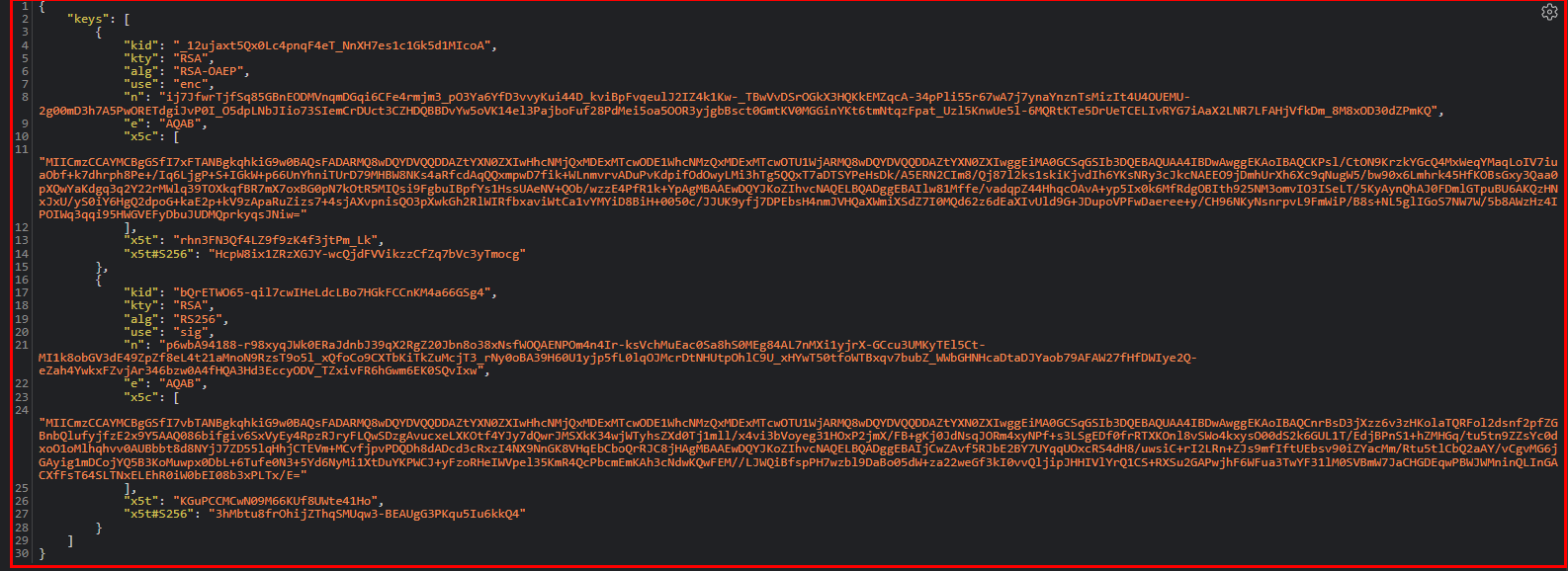
In the web browser, navigate to the hyperlink for the “jwks_uri” parameter copied above and make a note of the key.
IAM
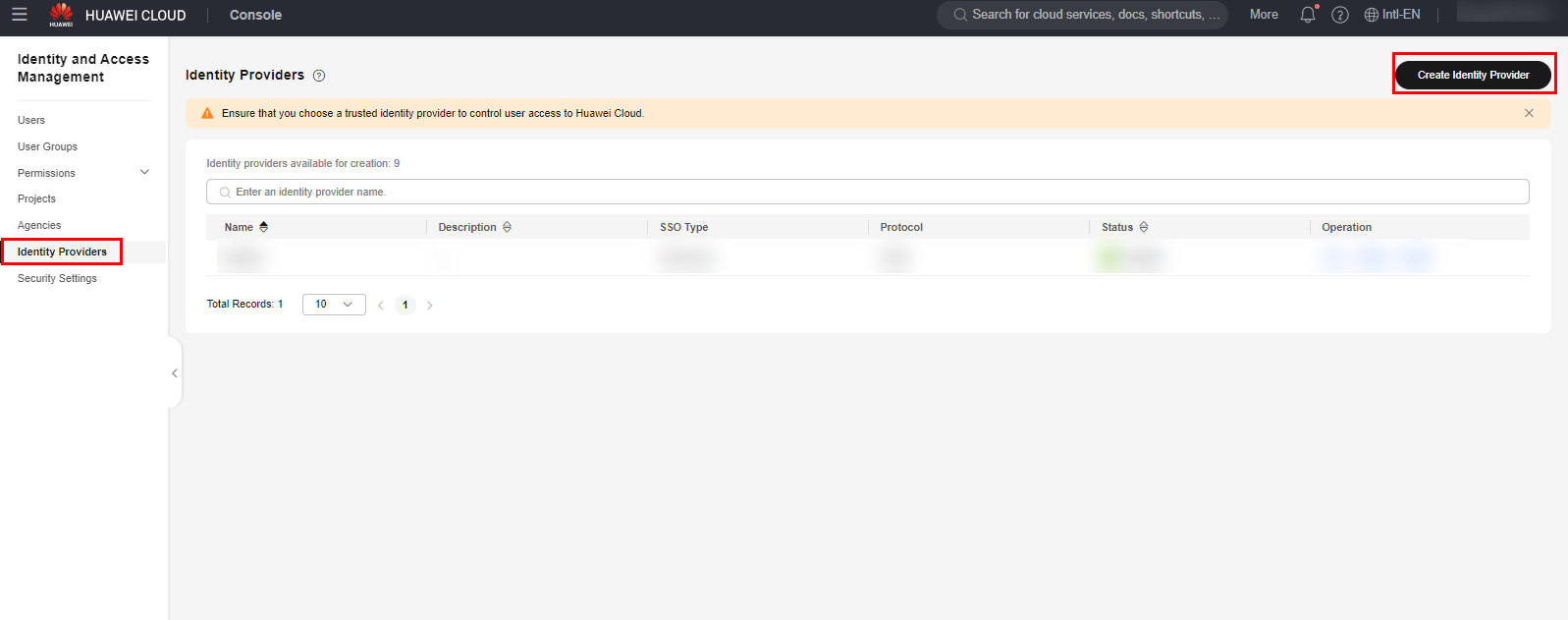
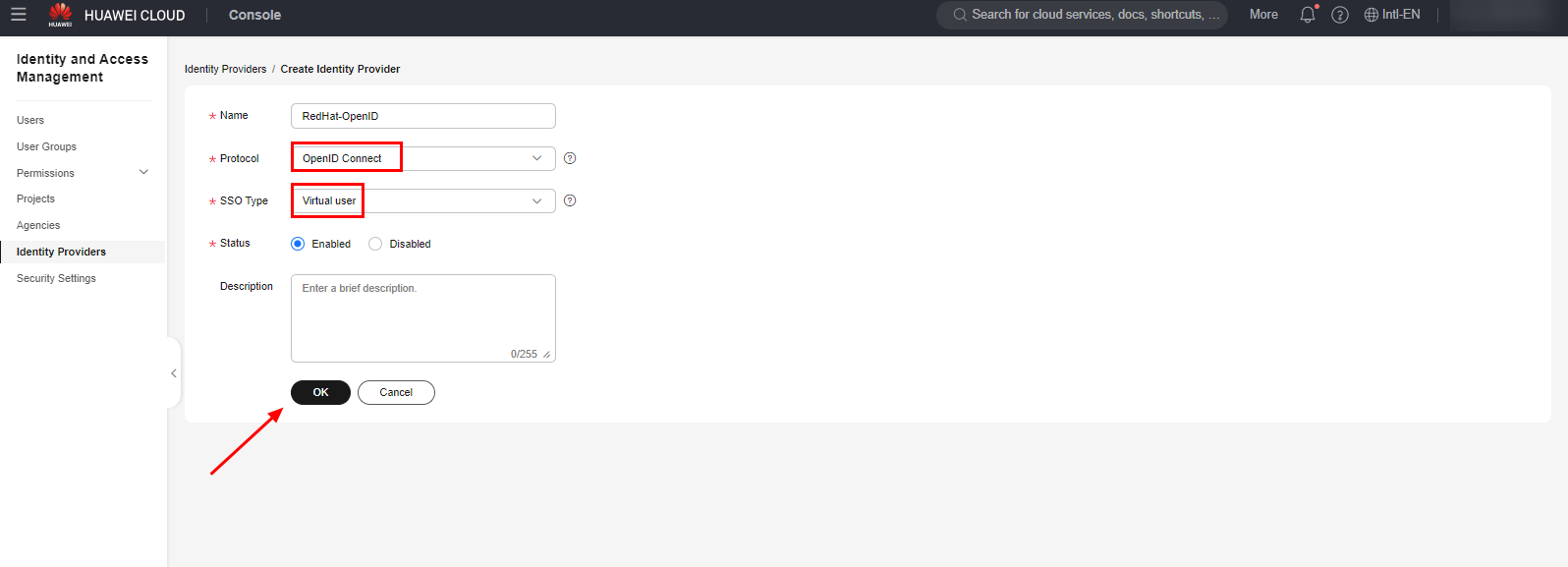
Access the IAM service in the Huawei Cloud console and navigate to the “Identity Providers” section. Click “Create Identity Provider” to create an identity federation configuration.
Select the OpenID-Connect protocol and the “SSO Type” as “Virtual User”.
Click the “OK” button to save the IdP creation settings.
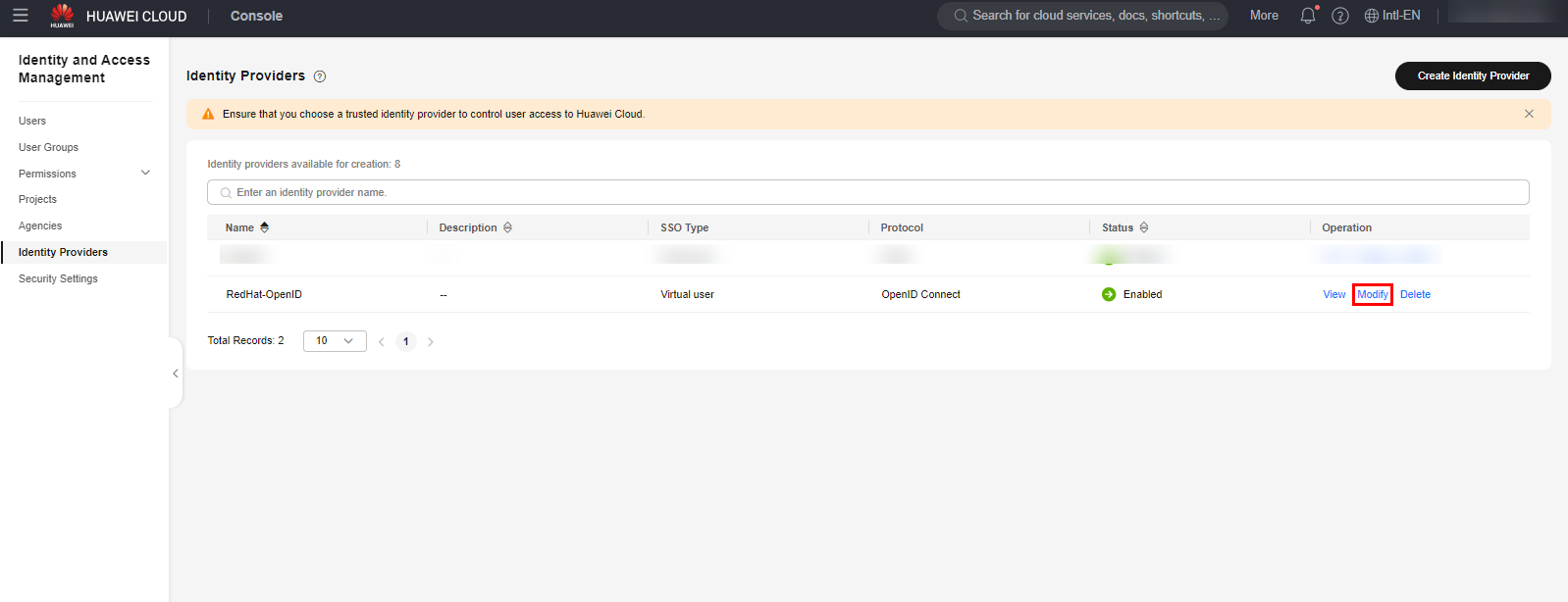
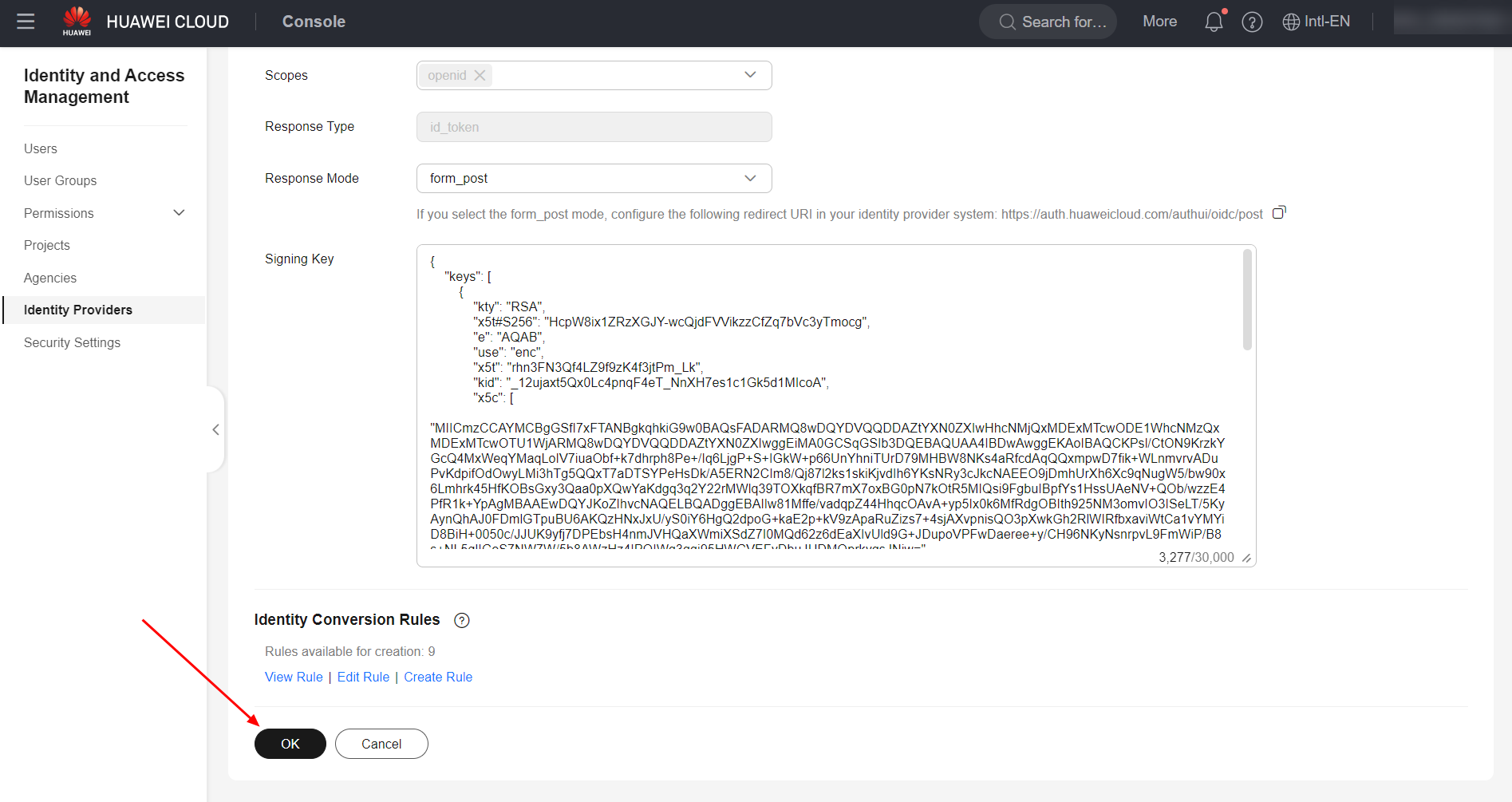
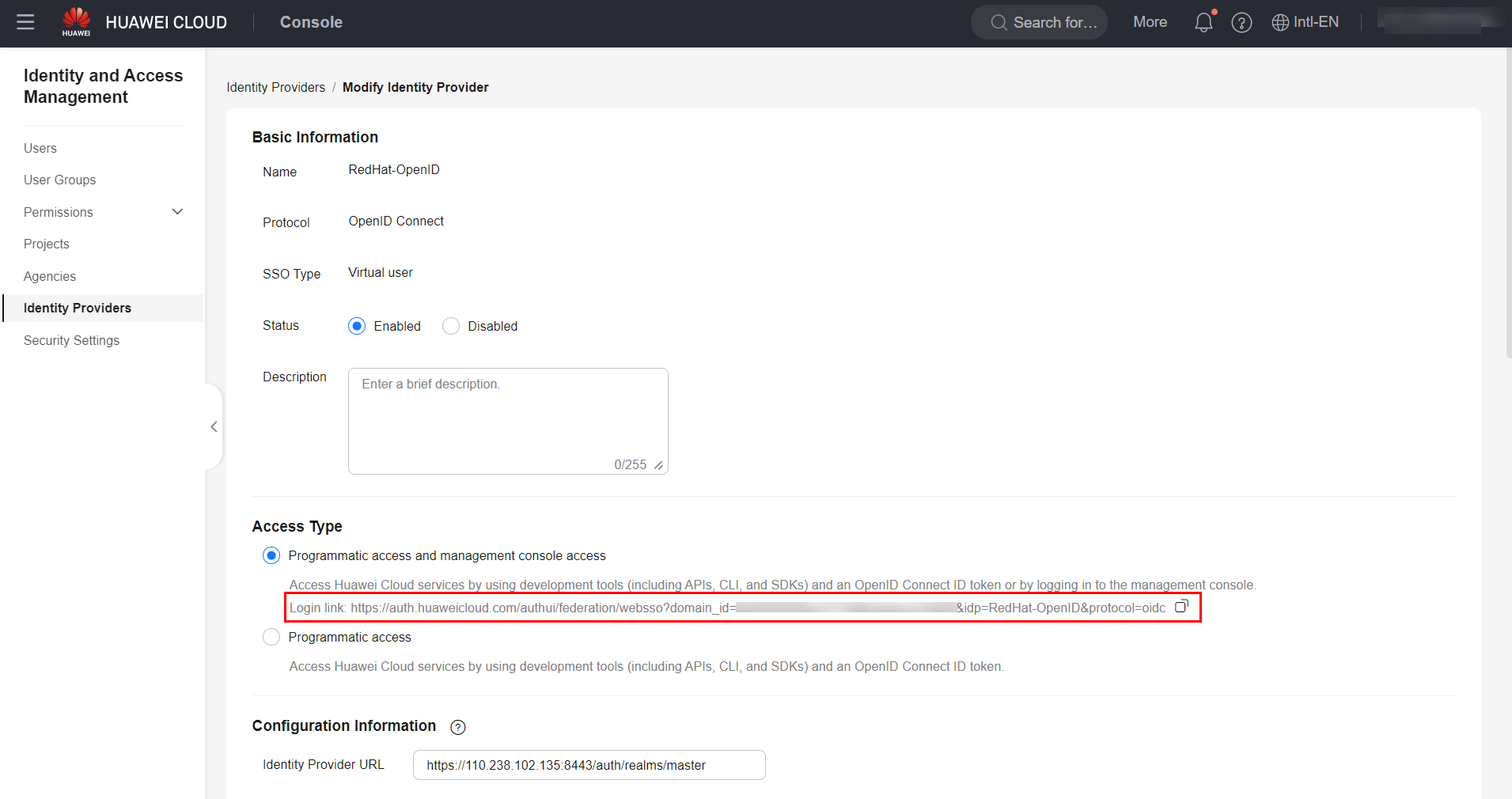
Once done, select the “Modify” option next to the created identity provider and fill in the fields as shown in the figure below.
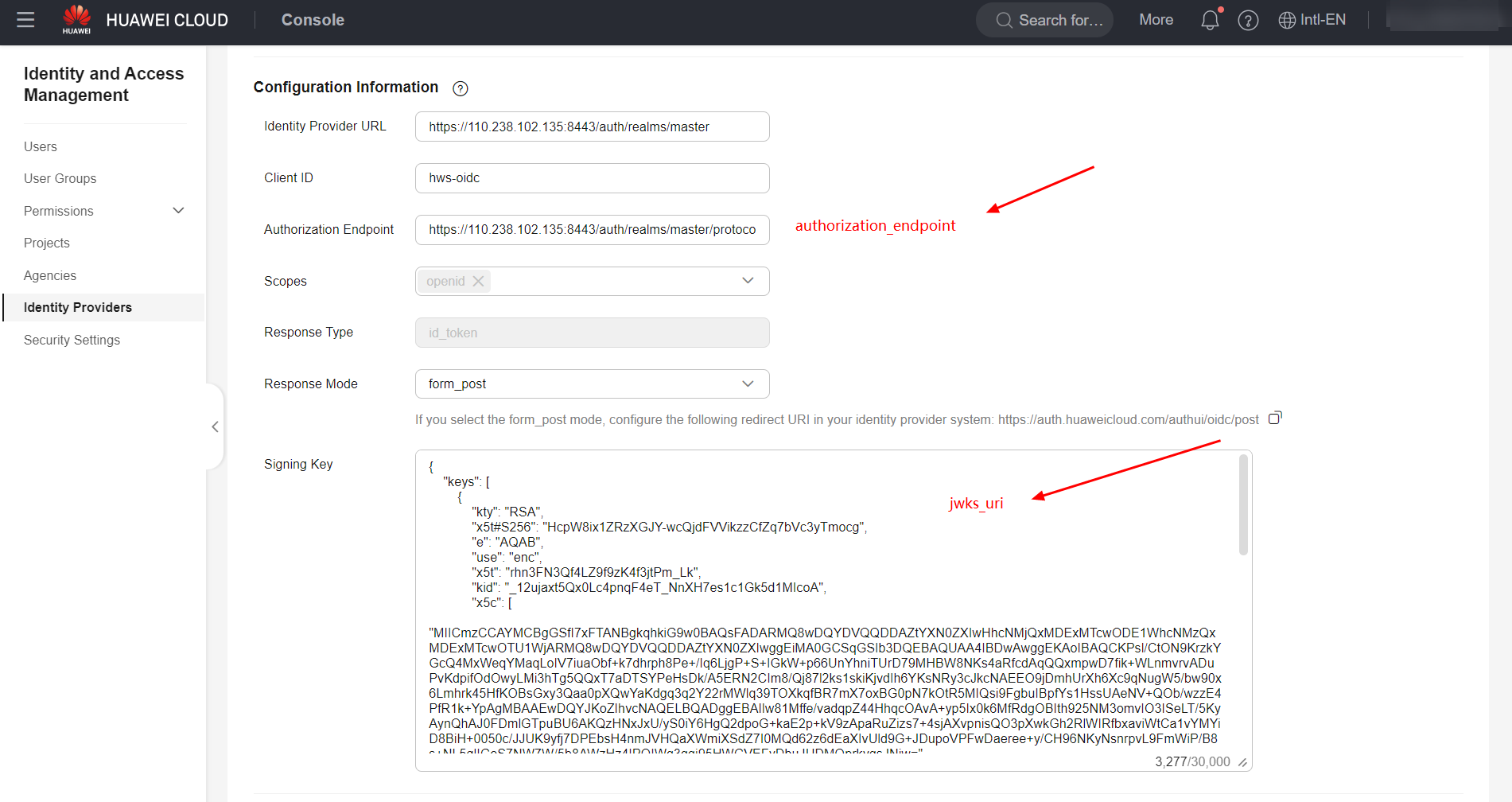
-
Identity Provider URL: Hyperlink relative to the realm in which the client was configured in keycloak. Example: ;
-
Client ID: Same parameter configured in the “Client ID” field of Keycloak;
-
Authorization Endpoint: Parameter “authorization_endpoint” present in the Open-ID endpoint configuration file in Keycloak;
-
Response Mode: “form_post”;
-
Signing Key: Contents of the “jwks_uri” parameter, present in the Open-ID endpoint configuration file in Keycloak.
Important: The Open-ID protocol necessarily requires an SSL certificate to be configured in the identity provider to enable communication via the HTTPS protocol. The SSL certificate can be a self-signed certificate. Finally, in the “Identity Conversion Rules” section, click “Create Rule” to create a rule for converting users and groups from the IdP to the corresponding users and groups in Huawei Cloud. You can use the following example conversion rule.
Important: The conversion rule below maps all Keycloak users to IAM groups in Huawei Cloud that have the same names as the groups configured in Keycloak. For example: In Keycloak, the user “Test” belonging to the “admin” group will be mapped, in Huawei Cloud, to the virtual user “Test” in the “admin” group. It is not necessary for the “Test” user to be previously created in Huawei Cloud. However, it is mandatory for the “admin” group to be previously created in Huawei Cloud with the appropriate access control policies.
[
{
"remote": [
{
"type": "username"
},
{
"type": "Group"
}
],
"local": [
{
"user": {
"name": "{0}"
}
},
{
"group": {
"name": "{1}"
}
}
]
}
]
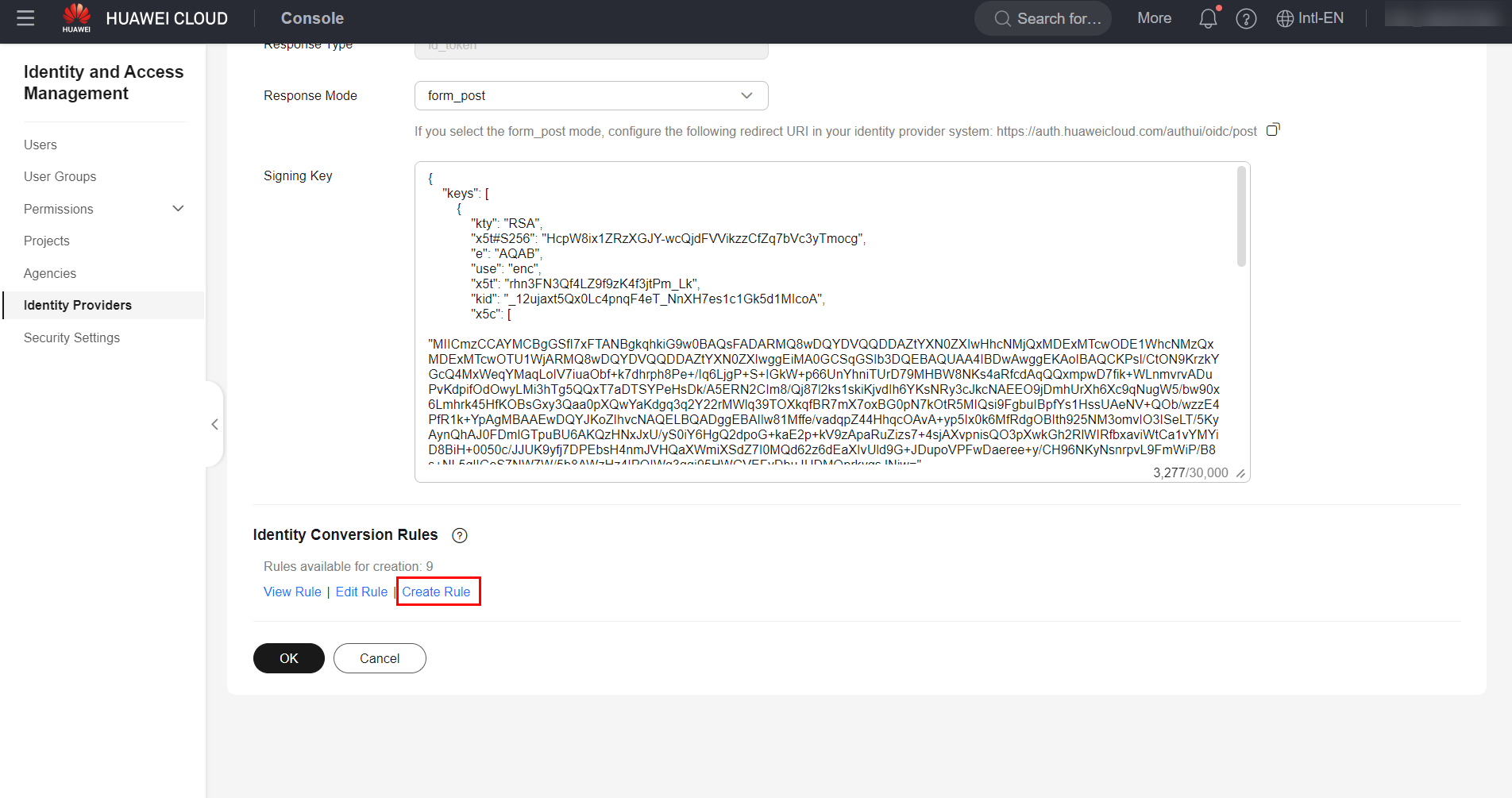
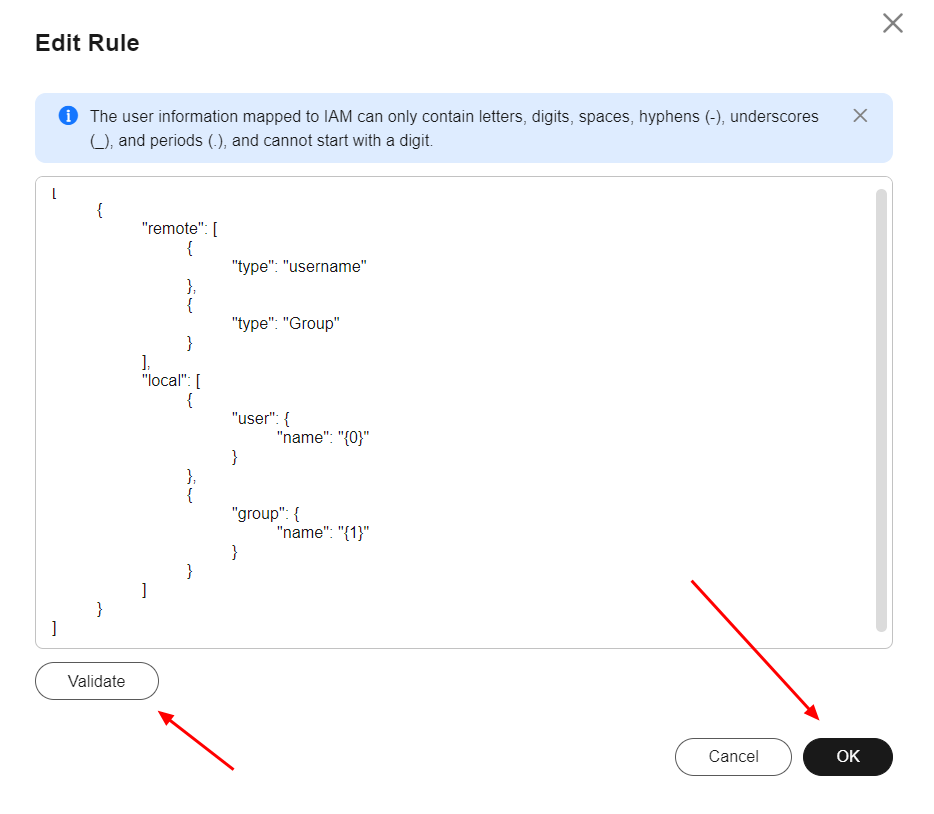
Once done, click “OK” to save the changes made to the IdP.
Example
The following is an example of validating login to the Huawei Cloud console through identity federation.
Accessing the Huawei Cloud console and selecting the option to log in through a federated user.
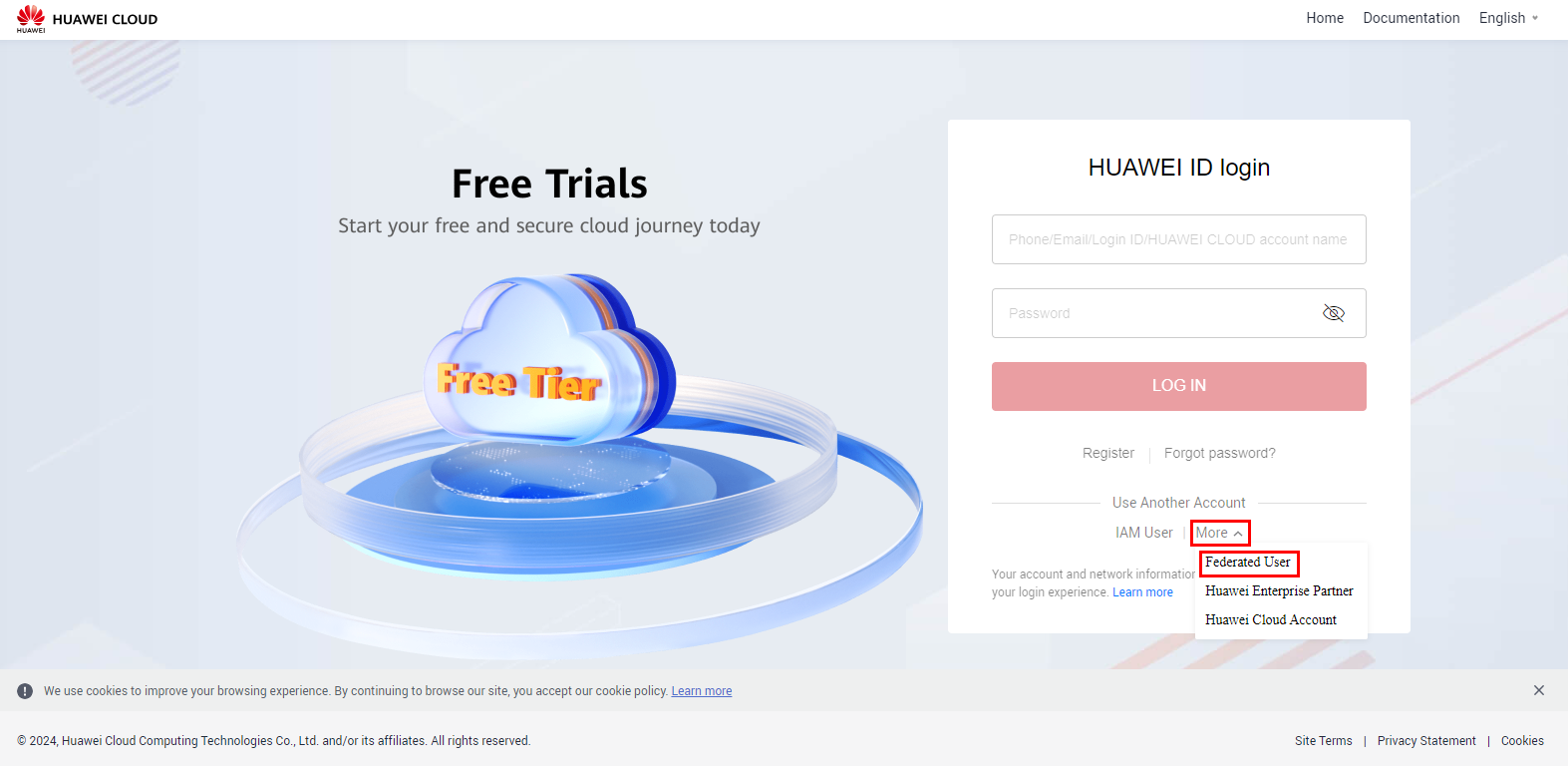
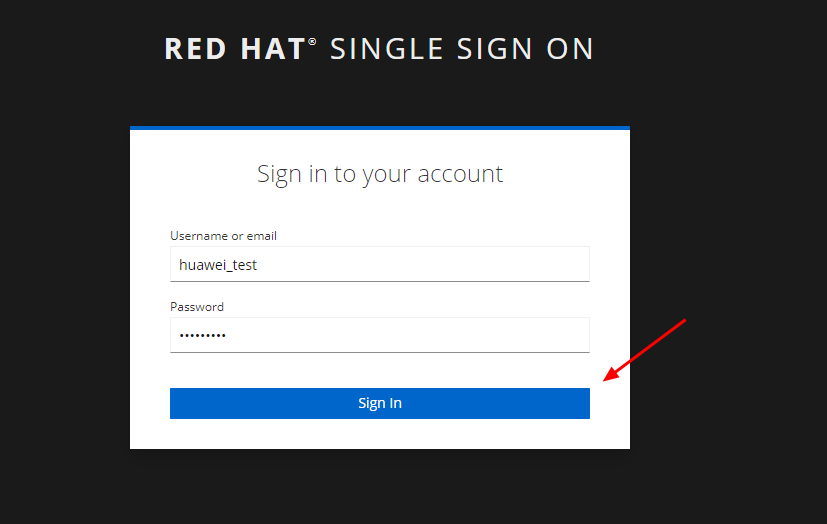
Entering the account name and selecting the configured IdP from the dropdown.
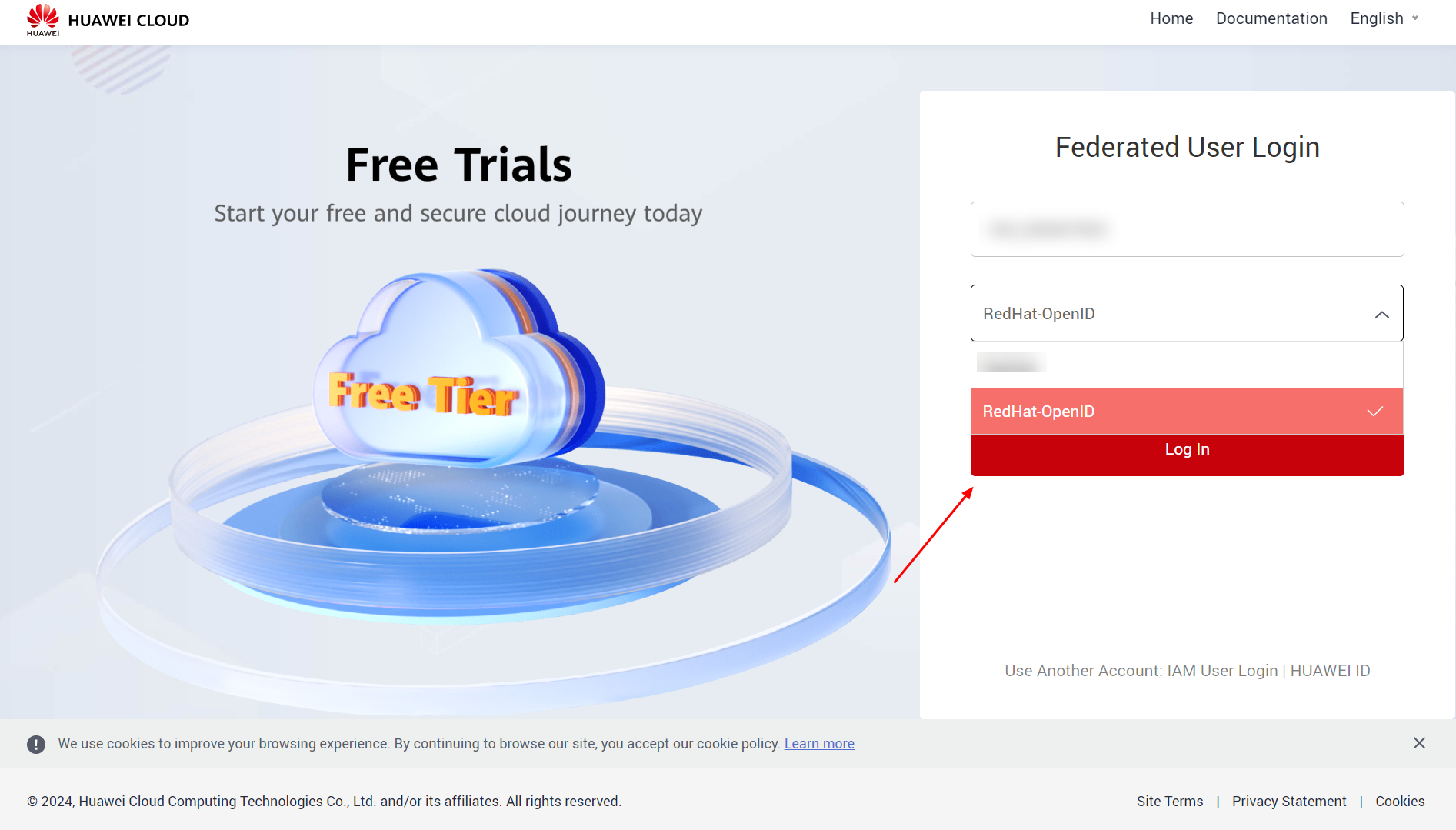
Logging in to the configured identity provider.
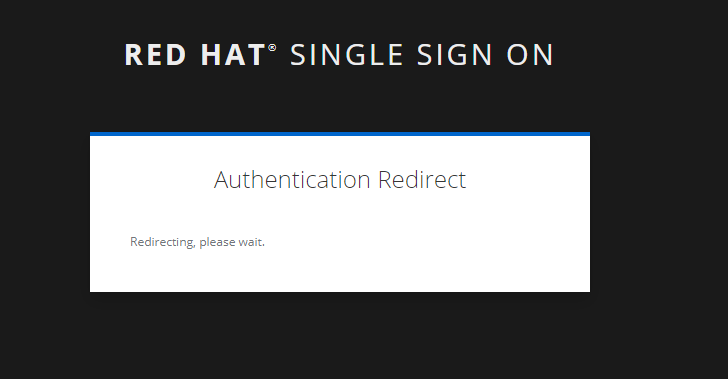
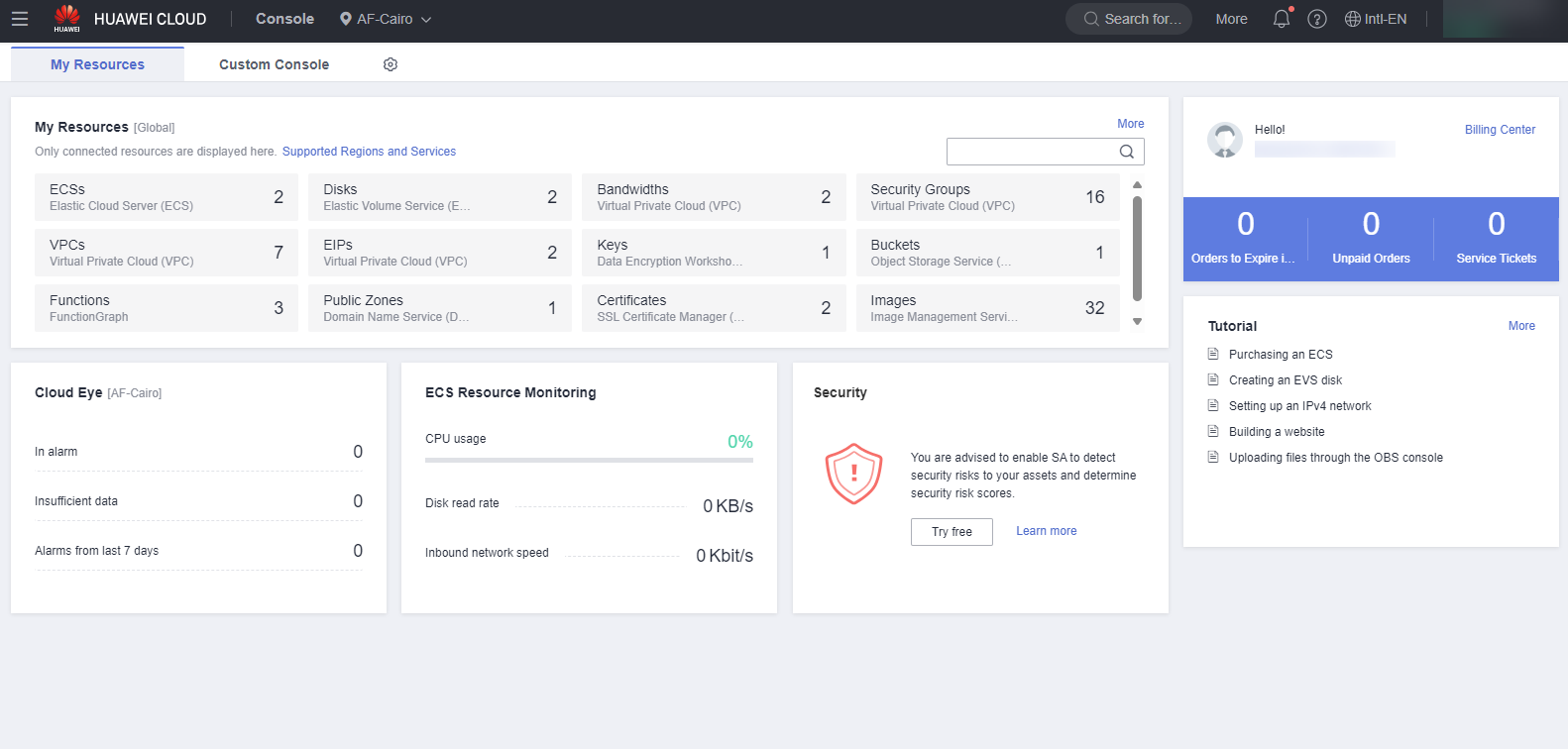
Authentication successful, redirecting to the Huawei Cloud console.
Important: You can also log in to the console through identity federation using the hyperlink generated in the Identity Provider configuration in the Huawei Cloud console.
References
-
IAM Documentation: https://support.huaweicloud.com/intl/en-us/usermanual-iam/iam_08_0002.html
-
Huawei Cloud Blog: https://bbs.huaweicloud.com/blogs/401343
